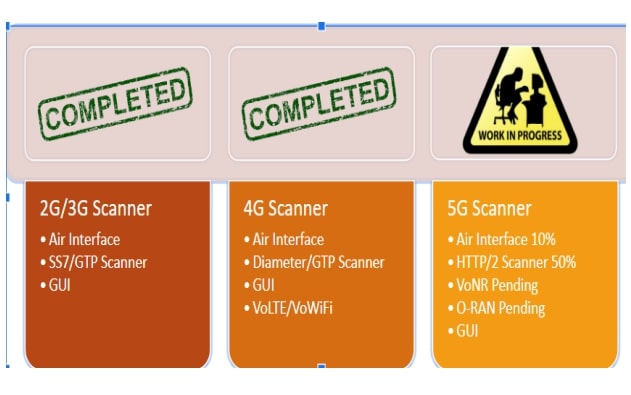
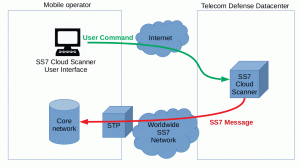
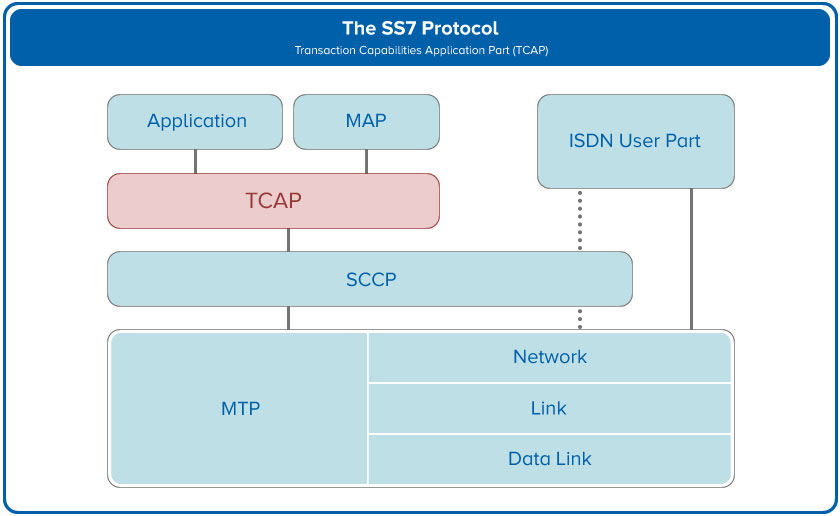
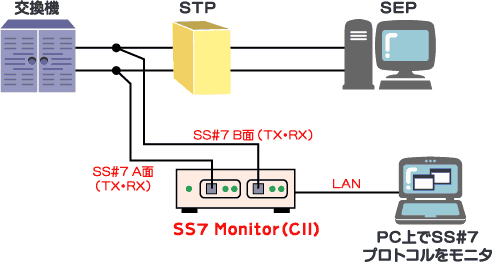
Telegram Hack using SS7 Attack | Apart from more sophisticated and advanced technologies available to Governments, Enterprises, Terrorist Groups and general hackers. This SS7 Attack... | By Blackphone SA | Facebook

Animals | Free Full-Text | The Use of a Brief Synchronization Treatment after Weaning, Combined with Superovulation, Has Moderate Effects on the Gene Expression of Surviving Pig Blastocysts