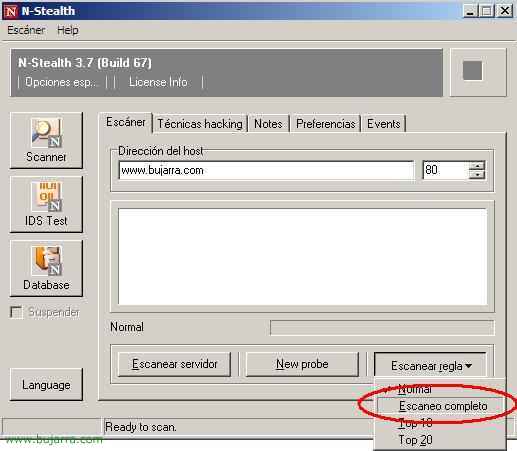
Vulnerability Scanning - CompTIA Network+ N10-006 - 3.1 - Professor Messer IT Certification Training Courses

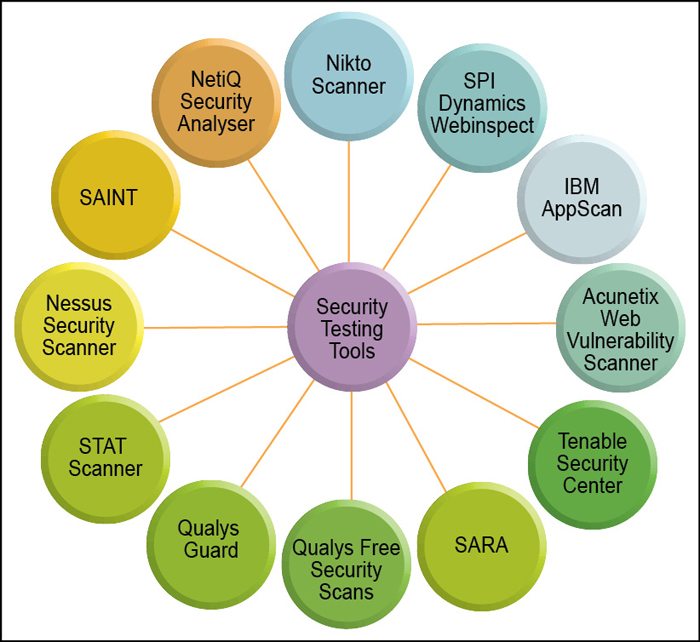
PPT - Chapter 11: Vulnerability Resources A vulnerability is a weakness that could be exploited PowerPoint Presentation - ID:3008381










/filters:no_upscale()/news/2020/04/trivy-docker-harbor/en/resources/11_r9Gtat1xatsOqhrleJEW_w-1587869509431.png)