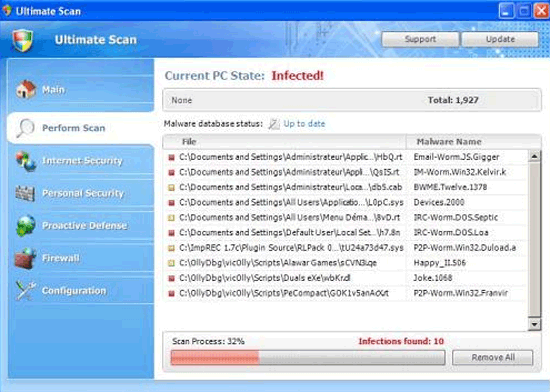
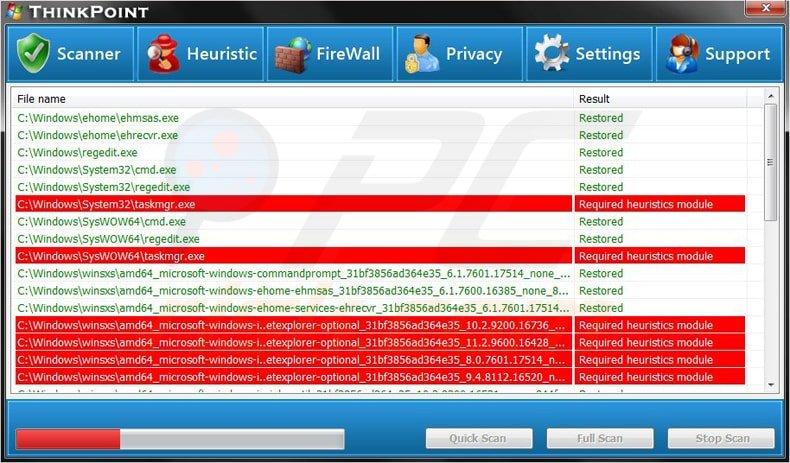
antimalware - What could be the source of various AVG "Exploits" (Rogue Scanner, Fake Video Player, Social Engineering, etc)? - Information Security Stack Exchange
Router Exploit Kits: An overview of RouterCSRF attacks and DNS hijacking in Brazil - Avast Threat Labs

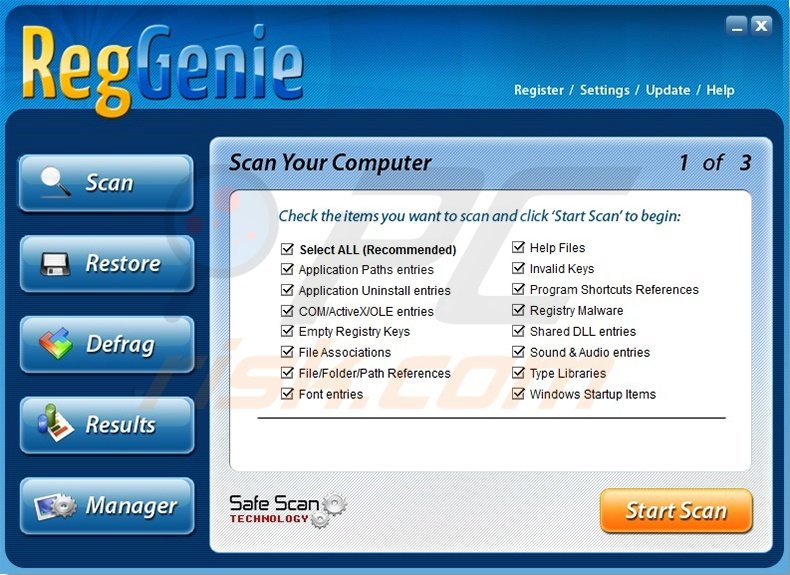







![KB3035] How do I use the ESET Rogue Application Remover (ERAR)? KB3035] How do I use the ESET Rogue Application Remover (ERAR)?](https://support.eset.com/storage/ESET/Platform/Publishing/images/Authoring/ImageFiles/ESET/KBTeamOnly/SOLN3035/SOLN3035Fig1-3a.png)





![Wi Ploit Wi Fi Exploit Tool - HackingPassion.com : root@HackingPassion.com-[~] Wi Ploit Wi Fi Exploit Tool - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/wp-content/uploads/2019/12/Wi-Ploit1.png)